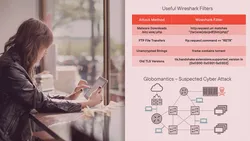
Identify Common Cyber Network Attacks with Wireshark 
This course provides an introduction to using Wireshark to identify common cyber network attacks and indicators of compromise. Participants will gain the skills to quickly spot malicious activity in network traffic. ▼
ADVERTISEMENT
Course Feature
![]() Cost:
Cost:
Free Trial
![]() Provider:
Provider:
Pluralsight
![]() Certificate:
Certificate:
Paid Certification
![]() Language:
Language:
English
![]() Start Date:
Start Date:
On-Demand
Course Overview
❗The content presented here is sourced directly from Pluralsight platform. For comprehensive course details, including enrollment information, simply click on the 'Go to class' link on our website.
Updated in [February 21st, 2023]
What does this course tell?
(Please note that the following overview content is from the original platform)
This course will teach you how to quickly spot cyber attacks and indicators of compromise in network traffic with Wireshark.
Cyber attacks are everywhere. Are they lurking in your network? Every IT professional needs to develop the skills with Wireshark to quickly spot them. In this course, Identify Common Cyber Network Attacks with Wireshark, you’ll gain the ability to threat hunt at the packet level. First, you’ll explore how network and OS Fingerprinting scans work and how to identify them. Next, you’ll discover how to spot indicators of compromise in malware infections. Finally, you’ll learn how to isolate botnet and data exfiltration traffic. When you’re finished with this course, you’ll have the skills and knowledge of threat hunting with Wireshark needed to identify common cyber network attacks on your network.What can you get from this course?
We consider the value of this course from multiple aspects, and finally summarize it for you from three aspects: personal skills, career development, and further study:
(Kindly be aware that our content is optimized by AI tools while also undergoing moderation carefully from our editorial staff.)
What skills and knowledge will you acquire during this course?
By taking this course, learners will acquire the skills and knowledge to identify common cyber network attacks with Wireshark. This includes the ability to use network and OS fingerprinting scans to detect malicious activity, spot indicators of compromise in malware infections, and isolate botnet and data exfiltration traffic. Learners will also be able to use their skills to threat hunt on their own networks. Additionally, they will gain an understanding of topics such as risk management, legal and ethical issues, and information assurance.
How does this course contribute to professional growth?
This course contributes to professional growth by providing learners with the skills and knowledge to identify common cyber network attacks with Wireshark. Learners will be able to use network and OS fingerprinting scans to detect malicious activity, spot indicators of compromise in malware infections, and isolate botnet and data exfiltration traffic. They will also be able to use their skills to threat hunt on their own networks. This course can help learners prepare for a career in cyber security, such as a Cyber Security Analyst, Network Security Engineer, Cyber Forensics Investigator, or Penetration Tester. It can also help learners pursue further education in the field of cyber security, such as a Bachelor of Science in Cyber Security, Master of Science in Cyber Security, Doctor of Philosophy in Cyber Security, or Certificate in Cyber Security.
Is this course suitable for preparing further education?
This course is suitable for preparing further education in the field of cyber security. Learners will gain a comprehensive understanding of Wireshark and how to use it to identify common cyber network attacks. They will also learn how to use network and OS fingerprinting scans to detect malicious activity, spot indicators of compromise in malware infections, and isolate botnet and data exfiltration traffic. This knowledge can be applied to a variety of cyber security related degree programs, such as a Bachelor of Science in Cyber Security, Master of Science in Cyber Security, Doctor of Philosophy in Cyber Security, or a Certificate in Cyber Security.
Course Provider

Provider Pluralsight's Stats at AZClass
Pluralsight ranked 16th on the Best Medium Workplaces List.
Pluralsight ranked 20th on the Forbes Cloud 100 list of the top 100 private cloud companies in the world.
Pluralsight Ranked on the Best Workplaces for Women List for the second consecutive year.
AZ Class hope that this free trial Pluralsight course can help your Wireshark skills no matter in career or in further education. Even if you are only slightly interested, you can take Identify Common Cyber Network Attacks with Wireshark course with confidence!
Discussion and Reviews
0.0 (Based on 0 reviews)
Explore Similar Online Courses

QuickBooks Online vs Xero Accounting Software

House Price Prediction using Linear Regression and Python

Python for Informatics: Exploring Information

Social Network Analysis

Introduction to Systematic Review and Meta-Analysis
The Analytics Edge

DCO042 - Python For Informatics
Causal Diagrams: Draw Your Assumptions Before Your Conclusions

Whole genome sequencing of bacterial genomes - tools and applications
Mastering TCP Analysis with Wireshark
Wireshark Traffic Analysis: Customizing the Interface ARP ICMP and DNS

Wireshark for Basic Network Security Analysis
 Related Categories
Related Categories
 Popular Providers
Popular Providers
Quiz
 Submitted Sucessfully
Submitted Sucessfully
1. What is the purpose of this course?
2. What will you learn in this course?
3. What will you be able to do after completing this course?
4. What will you learn about malware infections?


Start your review of Identify Common Cyber Network Attacks with Wireshark